Fairy stories …
Fairy stories are wonderful
because
they suggest a wider reality …
The idea is that
they
suggest wider issues
is that it?
TAXES
Yes TAXES,
It’s spun that Devoid Cameron, UK Prime Minister proposes – at the gate (and spun much before too (hu knows what goes on at the gate?)) is pursuing tax evaders and tax avoiders. Sorry DC, I have been very restrained (I think that I even like you after what I’m used to). [edit: I have so far been restrained. I’m uncertain how much longer I will be restrained – it is politics after all and it is said that all’s fair in love and politics – and I will be very involved then.}
The trouble is – of course – is that [edit: you} represent the tax [edit: avoiding] evading and tax evading filthy rich scum – and I stress that I consider that you represent them. Take for example Philip Green. Didn’t you give the tax evading shit a job in your cabinet? OK I can’t check it now, it’s late. My question is how can you now be promoting the idea that tax evasion is so bad when you have [edit: had] such close associations with such accomplished tax evaders in the past?
edit: 18 June 2013 00:32 am It really pissed me off that the last lot and all the shits that they represented and actually who they were repeater[edit: d not r] a[n]d shitness [sorry, that was inteded as a latin ad ;)] that they didn’t have any warning from me … what cnuts they were
01.00 am Anyway DC The trouble is that I [am] opposed to your policies and your actions and also to your boy Clegg. I can assure you that I have no intention of action other than what is regarded as within the democratic process. No doubt you will be aware that I campaigned against your predecessor Tony Bliar. I am very concerned that I am regarded as a suspected terrorist by UK legal authorities through my totally democratic actions.
later clarification: I am very concerned that I am regarded as a suspected or potential terrorist by UK legal authorities. I am a political activist. A political activist is not a terrorist UNLESS THIS IS A FASCIST STATE.
01.20 It doesn’t matter that I USE CAPITAL LETTERS. The issue is that I am regarded and harassed by police as a suspected terrorist. It follows that I can be subjected to over the top state extermination. Isn’t that one point that needs to be recognised here? That the state sat that’s a suspected terrorist and kill them without any recourse?
Isn’t that Gibraltar and the MURDER of Jean Charles de Menezes? I am the media as much as the corporate media. The difference is that I care for others and justice.
01:30 am Well the point is that I am a political activist and I have been a politicalactivist for many years. While I have reported events in many ways far better than normal channels I don’t think that makes me a reporter. That’s because a reporter is amployed and gets paid to report things …
Anyway, I have been a political activist and it appears that I am on my own with very little support. I know that I am regarded bu UK authorities – or at least I was until very recently – as a potential terrorist. I do think that people should support me in this respect because they can also be labelled – I don’t know the appropriate phrase you journalists and politician would use here. The police have got me and are behaving towards me as a suspected terrorist. I know this through their behaviour. You will be aware that UK cops kill suspected terrorists with far too many bullets according to a certian patternm.
About Prism’s covert spying UPDATED 14/06/13
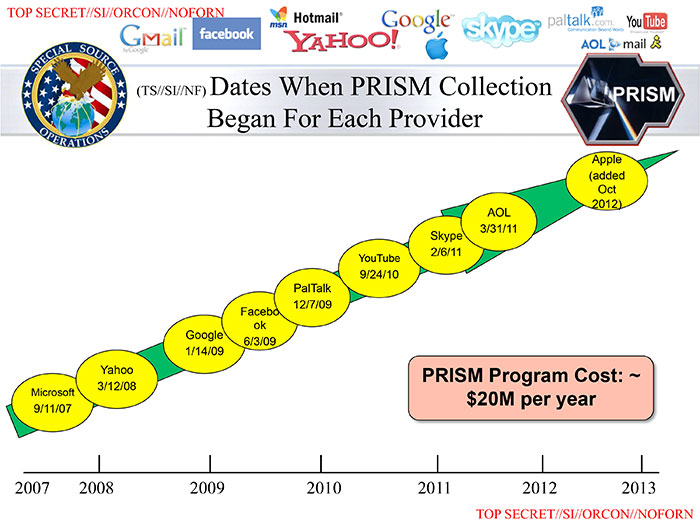
Prism, a clandestine system of spying on people involving many large internet companies was revealed by the newspapers the Washington Post and the Guardian on 6 June 2013 having – it is later revealed – been leaked by Edward Snowden.
The leaked documents revealed a routine, automated system of spying on people involving many of the largest internet companies – Microsoft, Yahoo, Google, Facebook, YouTube, Apple, etc. The leaked documents were in the form of a Powerpoint presentation presumably used to train intelligence agents. The Guardian further claimed on 7 June 2013 that the UK’s covert surveillance centre GCHQ had access to the NSA’s Prism system from at least 2010.
Prism raises some big issues: First, that people – including US citizens – are spied on as a matter of routine. Second, that huge internet companies have so readily assisted spying on people and then strangely denied it so strongly despite there being overwhelming evidence. Third, the closeness of huge corporations and the US state.
US and UK law is similar in that covert spying should be authorised rather than routine. The normal and expected procedure is that there exists an element of suspicion of some serious crime and some legal authority e.g. a warrant would be issued. Prism seems far more routine and relaxed. Safeguards to prevent US authorities spying on US citizens appear to be so weak as to be effectively useless.
Wikipedia suggests that gagging orders have been served on the big internet companies so they are legally prevented from disclosing their involvement in Prism. We have similar gagging orders in the UK under the Regulation of Investigatory Powers Act.
I was thinking more about interpreting the literal meanings of the carefully-crafted denials.
Microsoft: “We provide customer data only when we receive a legally binding order or subpoena to do so, and never on a voluntary basis. In addition we only ever comply with orders for requests about specific accounts or identifiers. If the government has a broader voluntary national security program to gather customer data we don’t participate in it.”
So they’ve had a legally binding order or subpoena to disclose information, only respond to specific accounts or identifiers (what about all or every? is that specific enough?) and don’t do it voluntary. Not nuch of a denial really.
Yahoo!: “Yahoo! takes users’ privacy very seriously. We do not provide the government with direct access to our servers, systems, or network.”
… but we do provide them with indirect access?
Google: “Google cares deeply about the security of our users’ data. We disclose user data to government in accordance with the law, and we review all such requests carefully. From time to time, people allege that we have created a government ‘back door‘ into our systems, but Google does not have a backdoor for the government to access private user data.”
According to law, no backdoor. What about the front door keys? ‘backdoor’ has a specific meaning which is about unauthorised access.
The internet is a network of servers. What if the NSA owned the servers that surround these internet companies? No need for a back door then. There’s no need to access a system if you can access all traffic that goes in and out. If I had a router on the internet I could inspect, store and analyse all traffic flowing through it: I just need to put it next – in the route – to an interesting machine.
I would be concerned by the closeness of government and corporatism [corporations] if I were some foreign governments. Where’s the payback? Are these corporations not going to use this spying technology for corporate advantage? There’s also the issue about Mussolini’s definition of Fascism. These corporations are playing along with the BS. Is there also a payback that they’re able to enrich themselves by evading taxes?
We live in an era of fake manufactured terrorism being the quite ridiculous dominant ideology. People are controlled through fear. Corrupt governments need to spy on their people to maintain control. There are very dangerous people that actually have a mind of their own. Governments and their political apointees will use this technology to corruptly maintain control. There are plenty of examples of USUK governments engaging in mass deception recently.
14/06/13 UPDATE
An interesting article here discusses US government spies ‘tapping’ AT&T in 2006:
In 2002, a visitor to his AT&T office in San Francisco identified himself as an NSA representative. The official interviewed Klein’s colleague, who said he was given top-secret government clearance soon after the encounter.
A year later when Klein he saw the colleague installing a special room, which only that person was allowed to enter.
When the colleague retired in 2004, he gave Mr Klein several documents, including highly technical wiring diagrams. The diagrams showed AT&T’s electronic communications flowed through a “splitter” which created identical copies of the digital material.
One copy continued on to its intended destination of consumer email in-boxes, phones and the like. The other copy flowed into the secret room.
It was clear that the NSA was looking at everything and not just foreign communications.
The article raises a number of issues:
- NSA is indiscriminate in collecting data
- It supports my earlier contention in the original article that it’s access to the data that is key rather than access to actual servers
- Concerning the ridiculous denials by the corporations: Language is key to these denials. Technical language from the domain of networking is used to obfuscate the debate: There is no need for access to ‘servers’ or a ‘back door’ if you have access to a ‘router’, a ‘feed’, a ‘split’ or a ‘tap’.
Update
Well I’m sorry that I haven’t managed much progress on the committed Prism post. I’ve been arranging / configuring a tor proxy and it’s taken all day. I could have done it much quicker on Linux but I’ve been running OpenBSD for the past three weeks or so and it’s different and I’m still getting used to it.
I’ll get on the case with the Prism post later today. It’s going to be looking at the revelations and the carefully-crafted denials and that
love you too
[later edit: If you have the facilities and ability to run a tor relay or bridge please consider it]